| Menu Path : System State>Audit Log |
Read Access Rights:
|
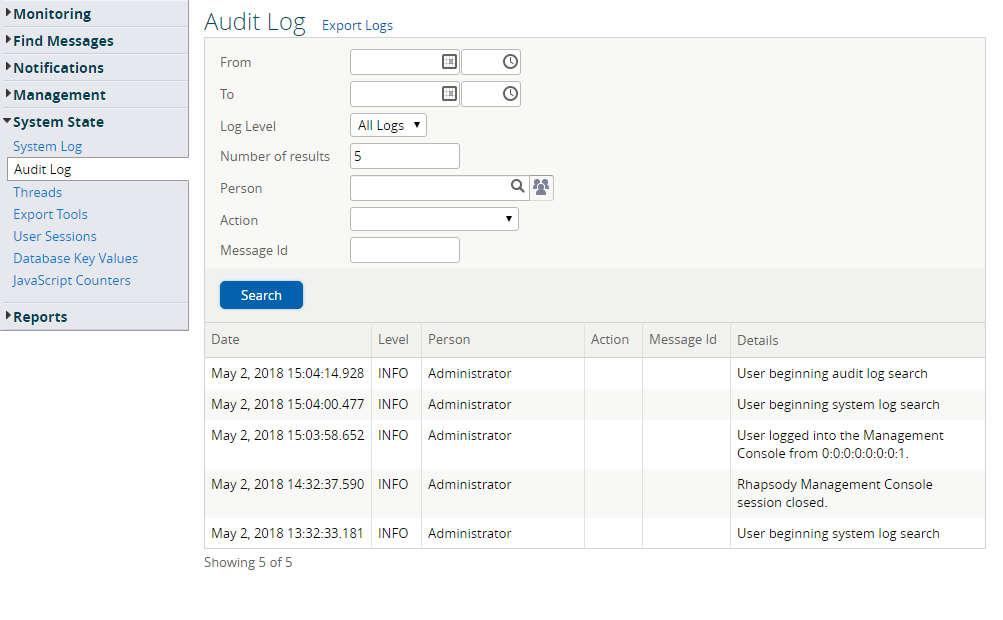
The Audit Log enables administrators to view all audit events between a specified time period or for a specific user.
Searching Audit Logs
To search audit logs:
Using the following search filters, search through the audit logs:
Field
Description
From
The date and time criteria to start the search from.
To
The date and time criteria to end the search at.
Log Level
The log level you want displayed. The available options are:
Off,Fatal,Error,Warn,Info,Debug,TraceandAll.Number of results
The number of log entries you want displayed on a page.
Person
To view the log details for a specific user:
- Enter the first few letters of the user's name in the field, and then select a user from the drop-down list.
- Select the Users icon and select a user from the Select User dialog to view audit logs for that user.
Action The type of action performed:
Message CreationMessage DeletionMessage ModifiedSearch QueryMessage ViewMessage ExportUser Privilege ChangeConfiguration ChangeAdministration Change
Message Id The message identifier of the message the action was performed on.
- Select the Search button to initiate a search.
Exporting Audit Logs
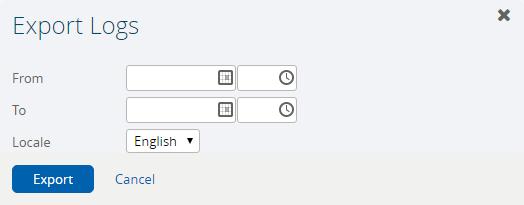
To export audit logs:
Click the Export Logs link to display the Export Logs dialog:
- Specify the From and To dates and times, select a Locale from the drop-down list, and select the Export button.
Audit Log Tampering Detection
An audit log tampering detection feature provides protection against malicious users attempting to edit the audit logs to hide their actions. If the audit log files on disk (located at <installationDirectory>/rhapsody/data/logs/audit) are modified by anything other than Rhapsody, this is reported as tampering in the system log, for example:
02 May 2018 11:46:02,689 | 31455 [WARN ] {Session-/127.0.0.1:49717}
(com.orchestral.rhapsody.admin.commands.usermanagement.ChangeUsersAndGroupsAdapter) The audit log has been tampered with.
Audit log tamper detection is disabled by default. It can be enabled through the rhapsody.properties file by setting the following property and restarting the engine:
| Property | Description |
|---|---|
LoggingService.auditLogTamperDetectionPeriod |
Specifies the period in hours which determines how often to run audit log tamper detection. It must have an integer value (otherwise the engine will not restart). Audit log tamper detection is disabled if the property is:
|