Whenever a Rhapsody engine is started, it checks whether it has been provided with an SSL certificate to use for these connections. If no certificate is found, it generates a new self-signed SSL certificate that is used for the Management Console and IDE connections. This SSL certificate is:
- Self-signed.
- A 2048-bit RSA key signed using SHA-256.
- Valid for five years from the time it is generated.
- Includes all hostnames that can be retrieved for the local machine (except for
localhost).
Using a generated self-signed certificate for secure communications with the engine results in a warning in the Rhapsody IDE and web browsers because the self-signed certificate would not have been verified by a third party trusted by the client. The warning is raised because anyone can create a certificate claiming to be whomever they choose. Refer to Untrusted Self-signed Certificate Warning for details.
You can suppress these warnings by explicitly trusting the self-signed certificate. During startup Rhapsody generates three files in the <Rhapsody>/rhapsody directory called managementConsole.sha1.txt, ide.sha1.txt, and soapApi.sha1.txt in order to assist with this process. These files contain the SHA-1 thumbprint of the SSL certificates used for the Management Console, IDE connection, and SOAP API respectively and can be used to verify that the certificate seen in the Rhapsody IDE or a web browser is the same certificate that Rhapsody is using.
Certificate generation can fail if Rhapsody is unable to determine any hostnames for the machine it is running on. If no alternative certificate has been provided for the IDE connection, Rhapsody would to fail to start. You can resolve this issue by fixing the hostname resolution on that machine so Rhapsody can retrieve the hostname, however, it can be circumvented by using a custom SSL certificate.
Thumbprints
For an RSA key, the thumbprint is the MD5 value of the encoded key, which is the algorithm name followed by the public exponent and the modulus. For a DSA key, the encoded format is the algorithm name followed by the parameters P, Q, G, and Y (in that order).
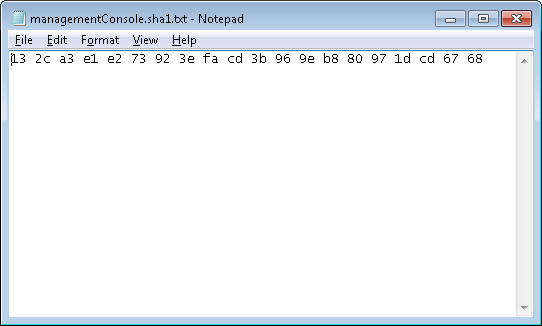
An example of a thumbprint in the managementConsole.sha1.txt is depicted in the following screenshot:
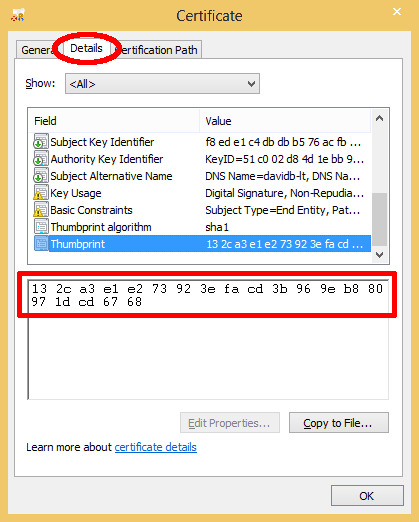
This SHA-1 thumbprint can then be compared to the certificate thumbprint within a web browser connecting to the Management Console: