Configuring Microsoft Account authentication
By Rick Anderson, Pranav Rastogi, and Valeriy Novytskyy
This tutorial shows you how to enable your users to sign in with their Microsoft account using a sample ASP.NET Core project created on the previous page.
Creating the app in Microsoft Developer Portal
- Navigate to https://apps.dev.microsoft.com:
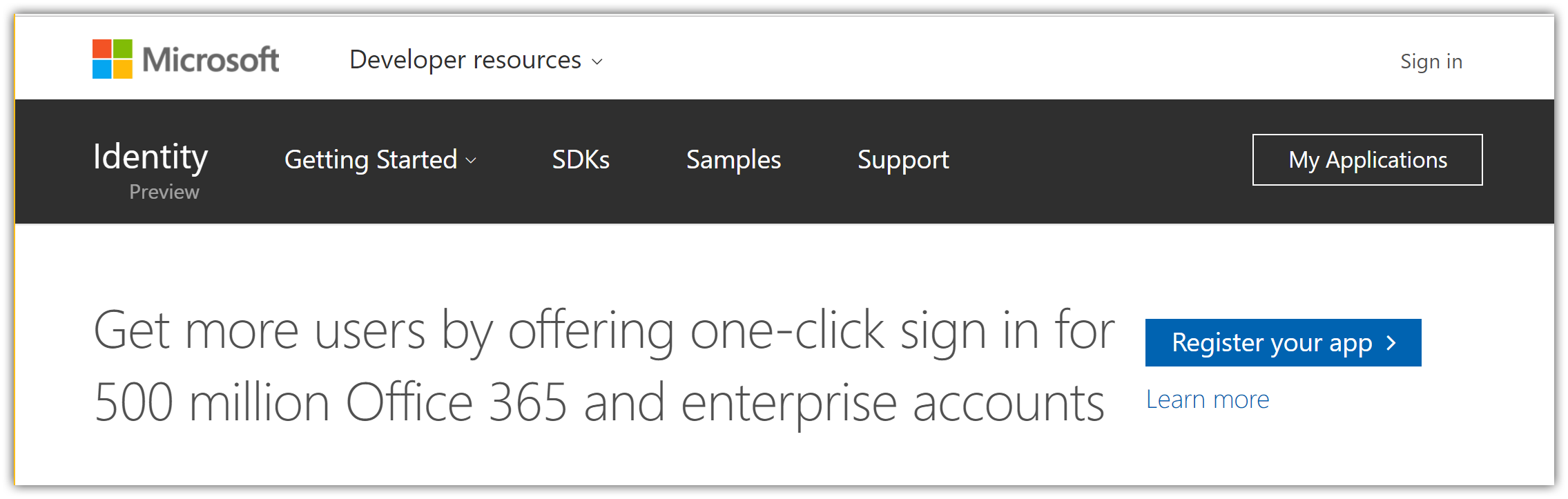
- Tap sign in:
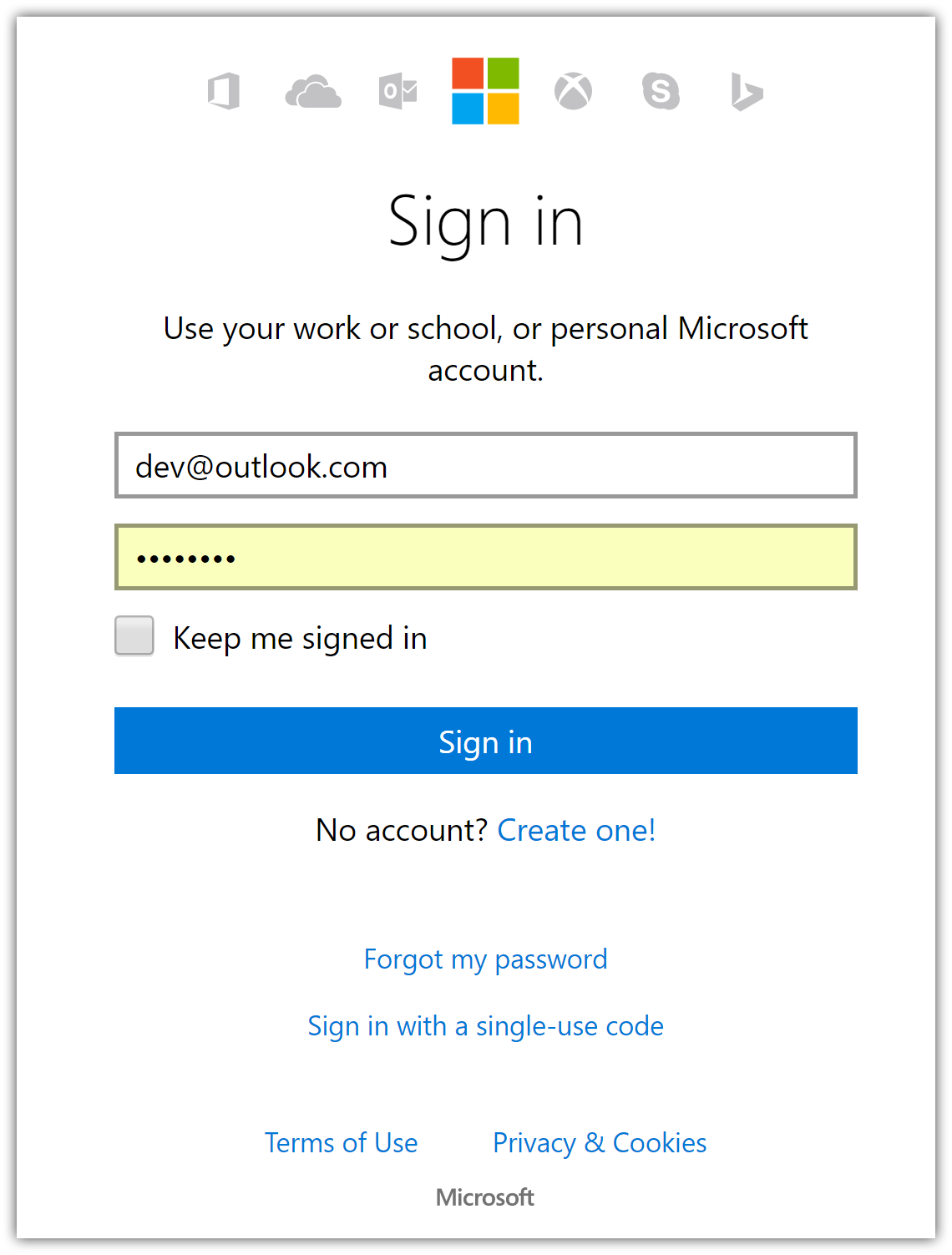
If you don't already have a Microsoft account, tap Create one!. After signing in you are redirected to My applications page:

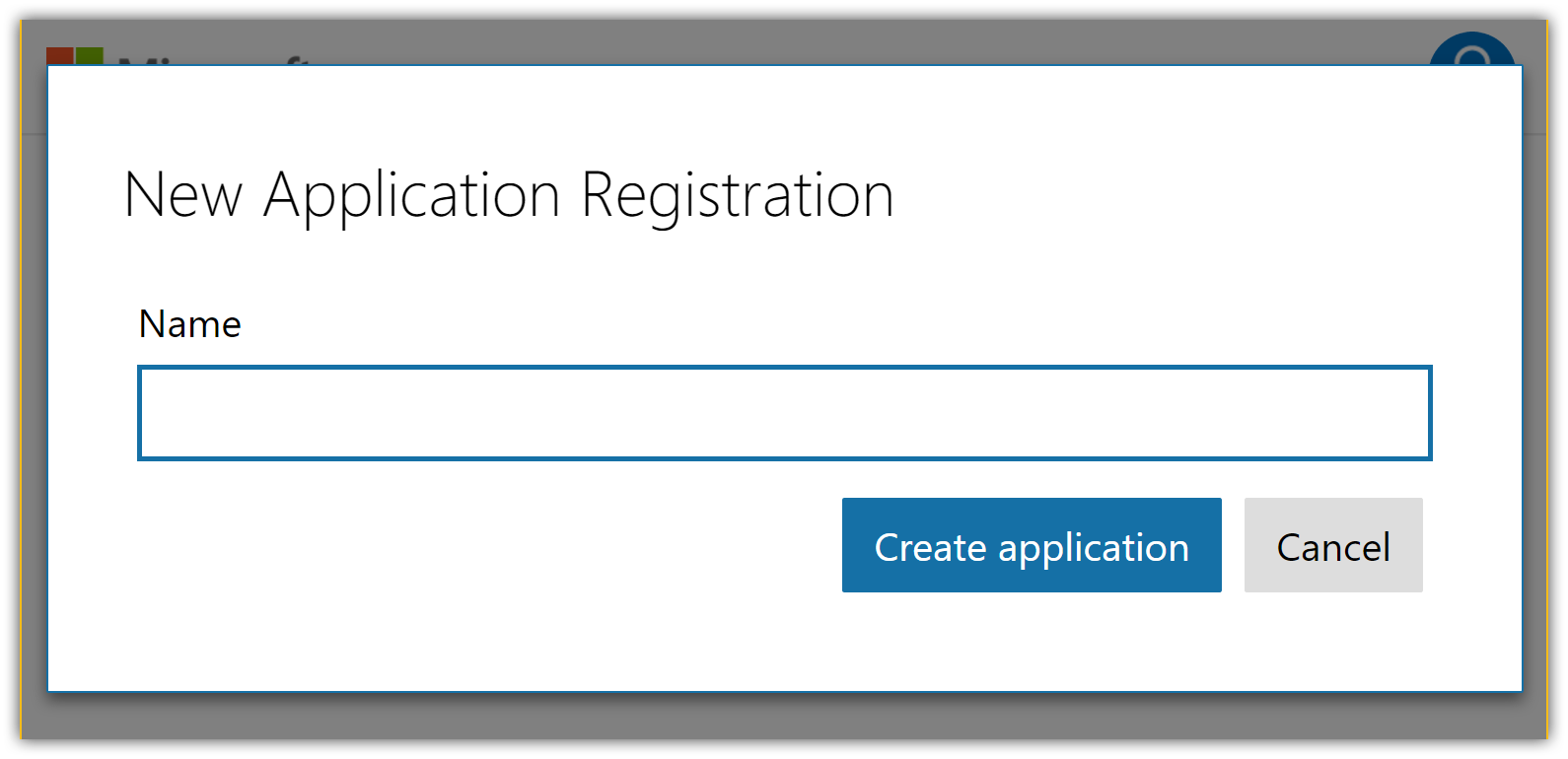
- Tap Add an app in the upper right corner and enter your application name:
- The Registration page is displayed:
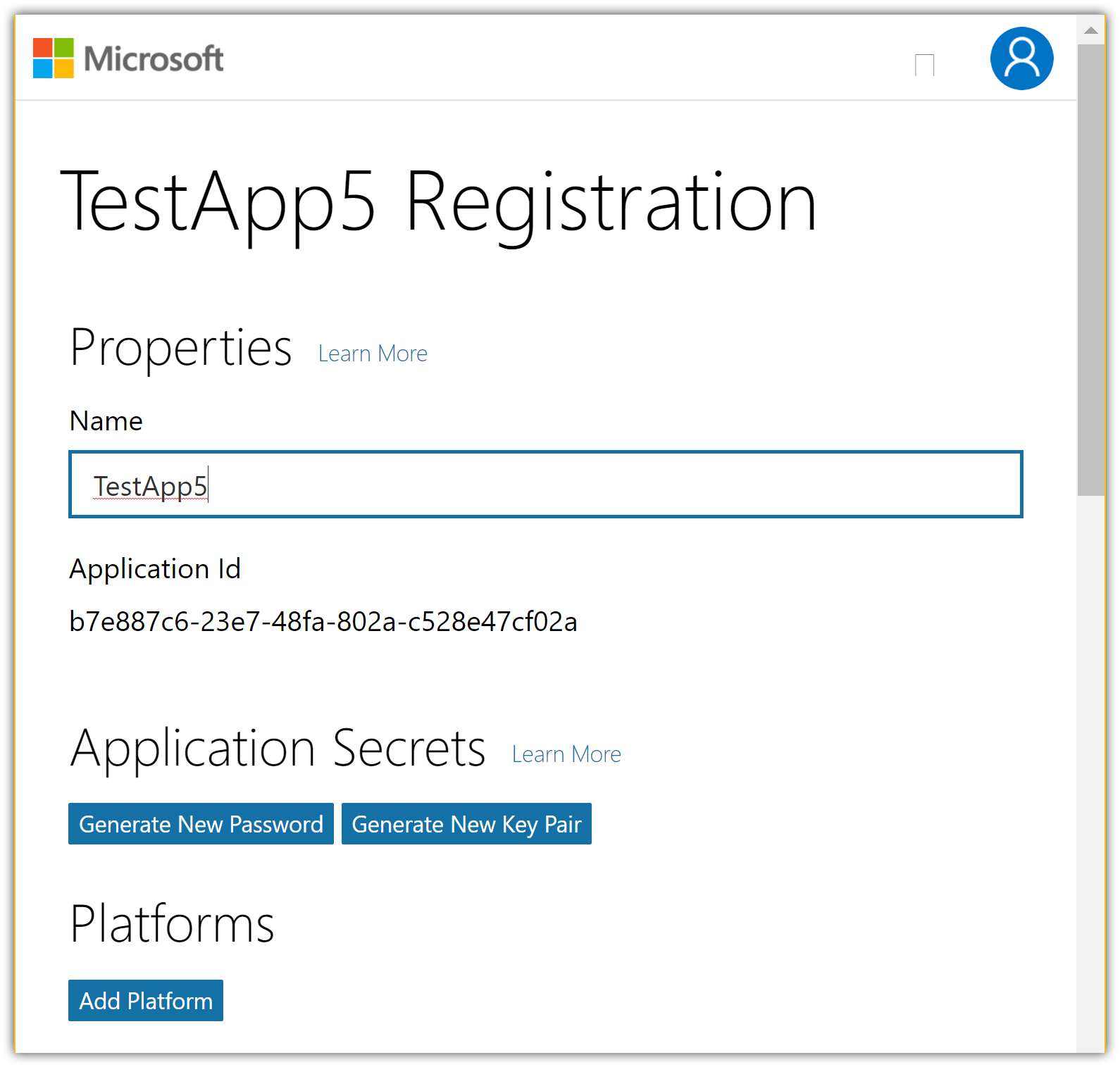
- Tap Add Platform in the Platforms section and select the Web platform:
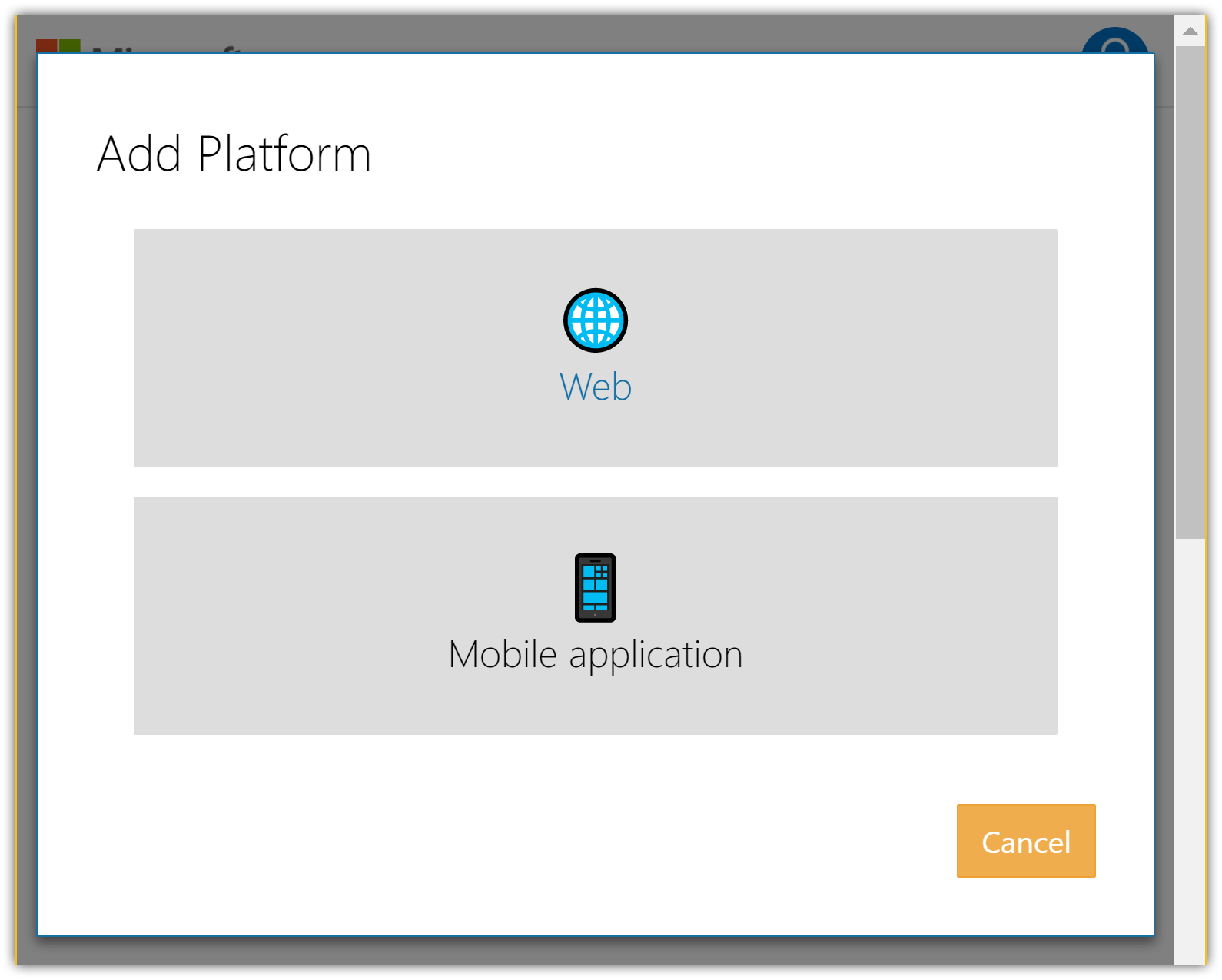
- In the new Web platform section, enter your current site URL with signin-microsoft appended into the Redirect URIs field. For example,
https://localhost:44320/signin-microsoft:
备注
When deploying the site you'll need to register a new public url.
备注
You don't need to configure signin-microsoft as a route in your app. The Microsoft Account middleware automatically intercepts requests at this route and handles them to implement the OAuth flow.
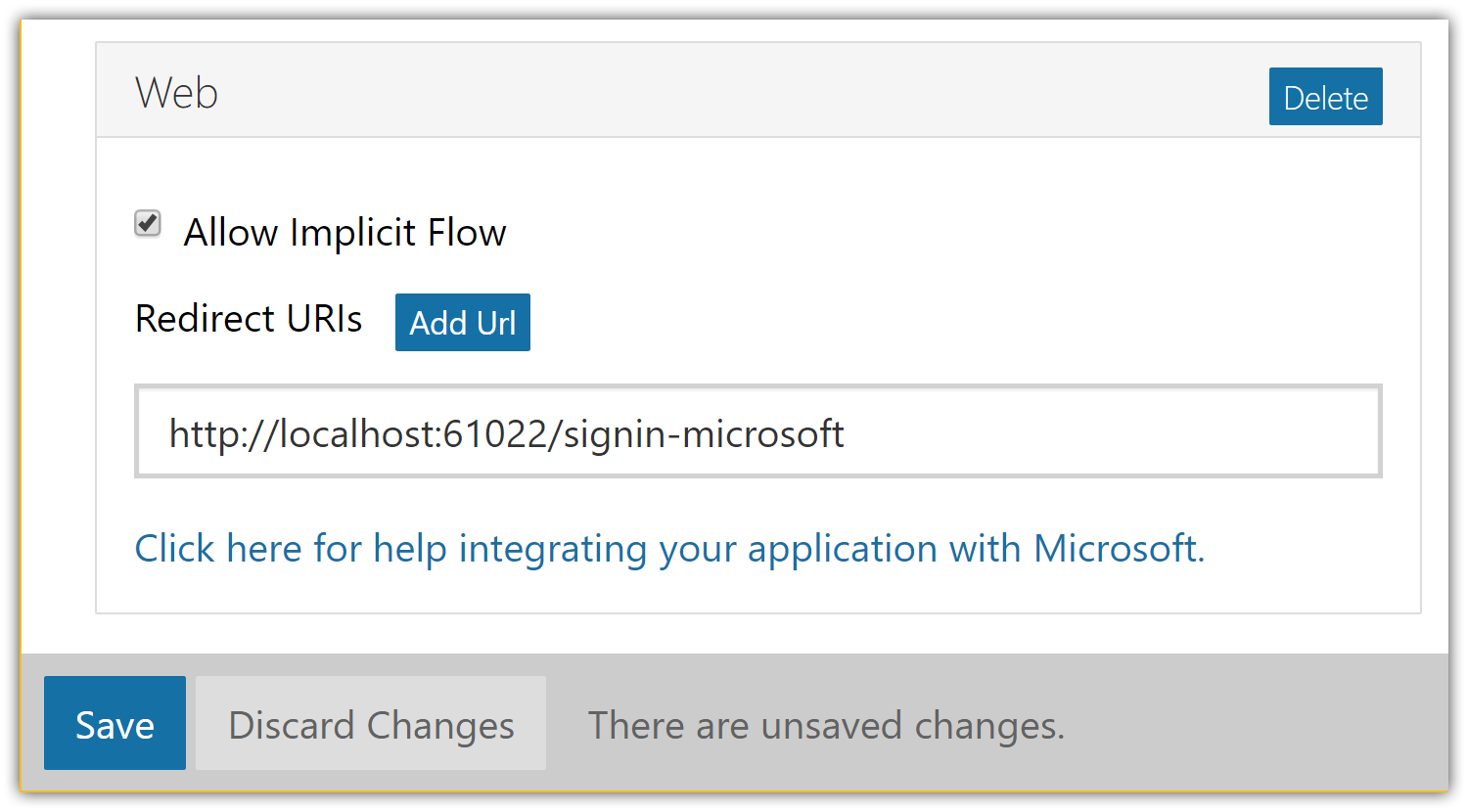
Don't forget to tap Add Url to ensure the Url was added.
Tap Save to save changes.
Storing Microsoft ApplicationId and Secret
Link sensitive settings like Microsoft ApplicationId and Secret to your application configuration by using the Secret Manager tool instead of storing them in your configuration file directly, as described in the social login overview page.
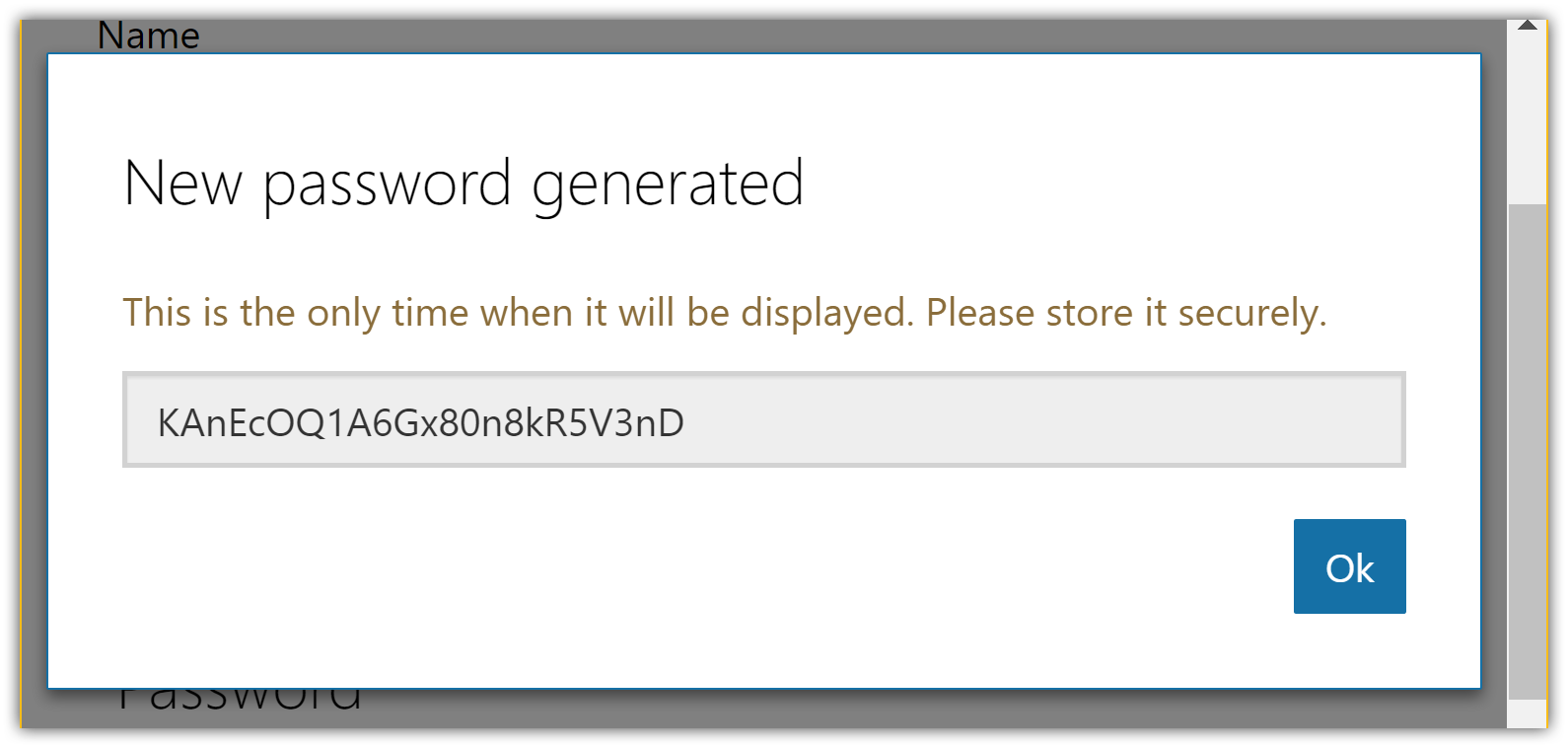
Note the
Application Iddisplayed on the Registration page.Tap Generate New Password in the Application Secrets section. This displays a box where you can copy the application secret:
Execute the following commands in your project working directory to store the Microsoft secrets:
dotnet user-secrets set Authentication:Microsoft:ClientId <client-id> dotnet user-secrets set Authentication:Microsoft:ClientSecret <client-secret>
The following code reads the configuration values stored by the Secret Manager:
public Startup(IHostingEnvironment env)
{
var builder = new ConfigurationBuilder()
.SetBasePath(env.ContentRootPath)
.AddJsonFile("appsettings.json", optional: true, reloadOnChange: true)
.AddJsonFile($"appsettings.{env.EnvironmentName}.json", optional: true);
if (env.IsDevelopment())
{
// For more details on using the user secret store see http://go.microsoft.com/fwlink/?LinkID=532709
builder.AddUserSecrets<Startup>();
}
builder.AddEnvironmentVariables();
Configuration = builder.Build();
}
Enable Microsoft Account middleware
备注
Use NuGet to install the Microsoft.AspNetCore.Authentication.MicrosoftAccount package if it hasn't already been installed. Alternatively, execute the following commands in your project directory:
dotnet add package Microsoft.AspNetCore.Authentication.MicrosoftAccount
Add the Microsoft Account middleware in the Configure method in Startup.cs:
app.UseMicrosoftAccountAuthentication(new MicrosoftAccountOptions()
{
ClientId = Configuration["Authentication:Microsoft:ClientId"],
ClientSecret = Configuration["Authentication:Microsoft:ClientSecret"]
});
Sign in with Microsoft Account
Run your application and click Log in. An option to sign in with Microsoft appears:
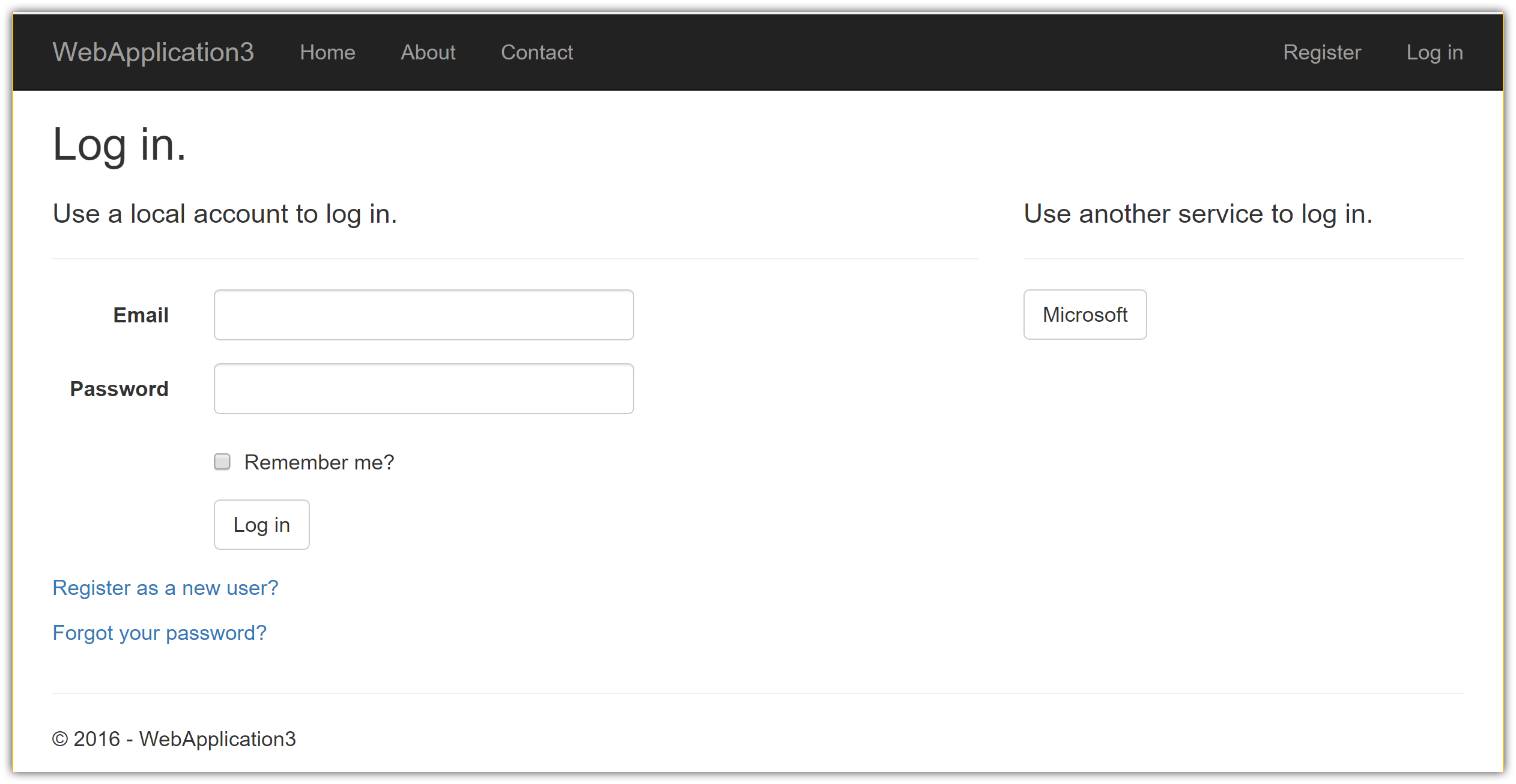
When you click on Microsoft, you are redirected to Microsoft for authentication:
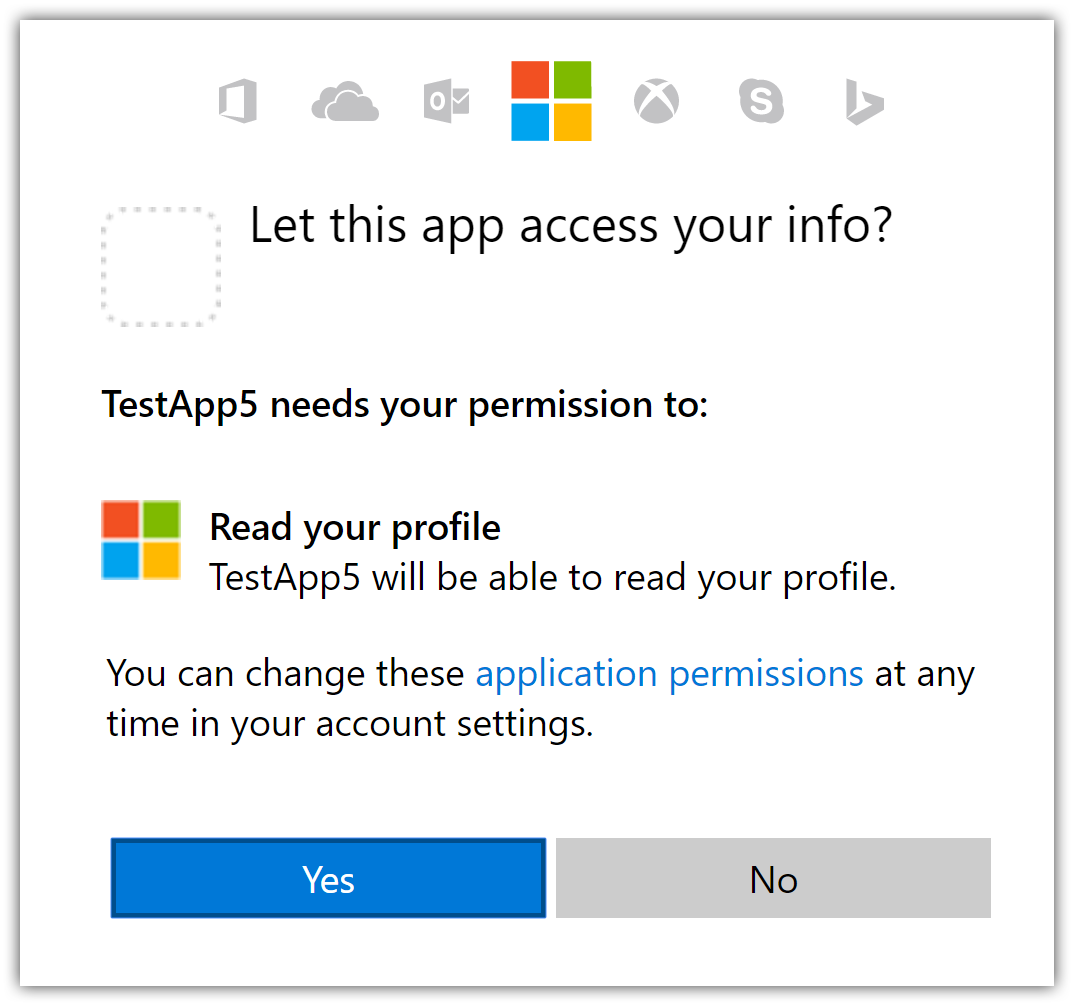
After entering your Microsoft Account credentials, you are redirected back to the web site where you can set your email.
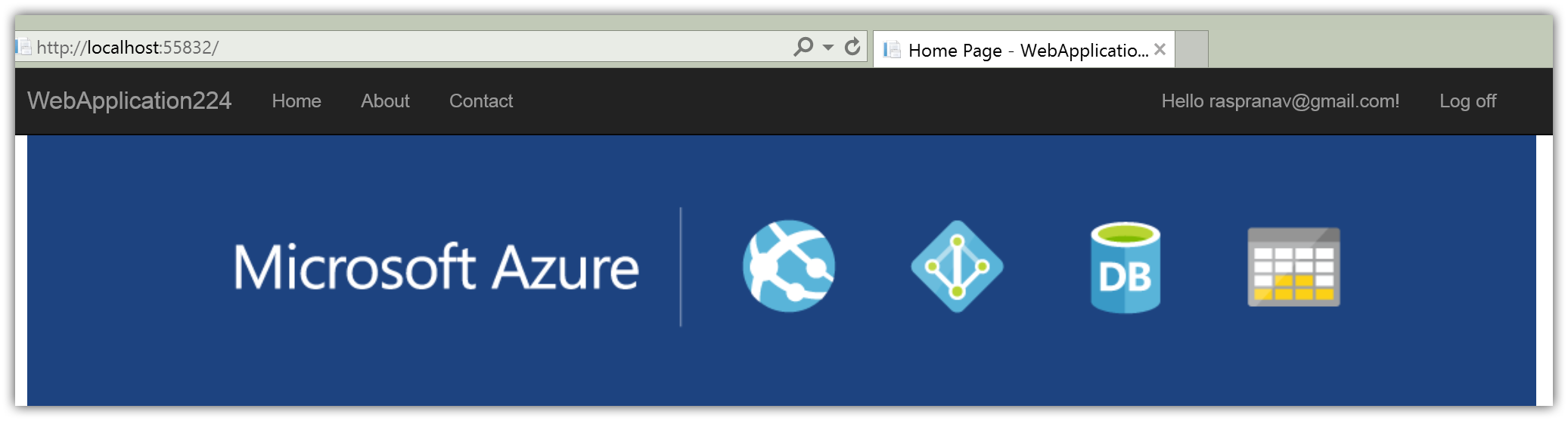
You are now logged in using your Microsoft credentials:
备注
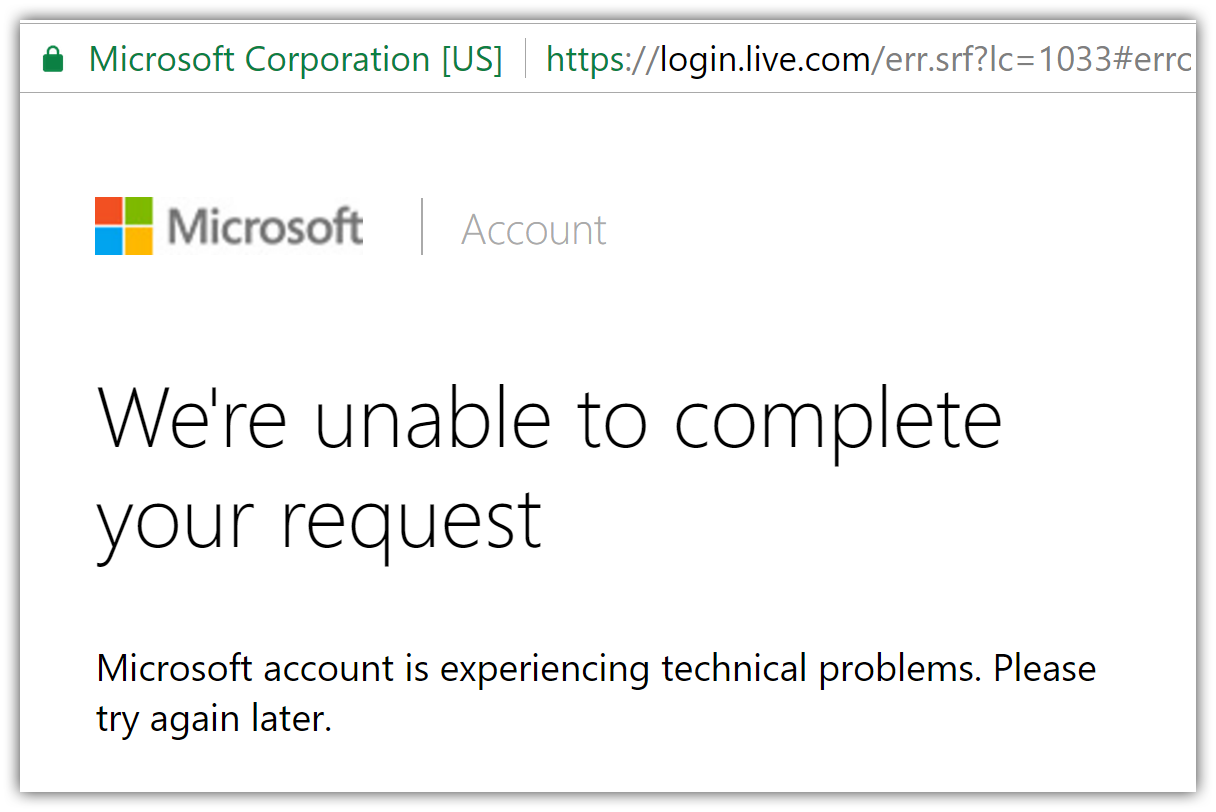
If the Microsoft Account provider redirects you to a sign in error page, note the error title and description directly following the # (hashtag) in the Uri. The most common cause is your application Uri not matching any of the Redirect URIs specified for the Web platform. In this case, ensure protocol, host, and port are all correct. Your application should be using https protocol and the redirect uri should end with signin-microsoft as that's the route Microsoft Account middleware requests the login provider to redirect to.
Next steps
This article showed how you can authenticate with Microsoft. You can follow a similar approach to authenticate with other providers listed on the previous page.
Once you publish your web site to Azure web app, you should reset the
Secretin the Microsoft developer portal.Set the
Authentication:Microsoft:ClientIdandAuthentication:Microsoft:ClientSecretas application settings in the Azure portal. The configuration system is set up to read keys from environment variables.