













I immediately had a decentralized crush on the Lisbon event. In the spirit of the event, Pierre picked up the template over on our live wiki and ran with it – when I asked him if he needed any help, he enthusiastically told me he was excited but set. We did a checkin call recently to followup and see where they’re going from here.
I work for a startup called Seedrs, been doing devops for almost two years. We are the first equity crowd funding platform in Europe. Interested in internet freedom! Really like the initiative, wanted to organize one. Found out about it through twitter somewhere. Found the description, said “let’s do it.”
To make for an accessible introductory activity, they started with by making DiscoSoupe. Everyone brings vegetables, chops and cooks, and then eats together. I love this, as an alternative to the usual “go out for a drink after.”
 The 15 gathered activists and hackers stood at a chalkboard in the street of the ancient district of Alfama in Lisbon as they did knoweldge shares around what the internet is, differences between circuit switching and packet switching. They were interested to understand protocol, IP, and public key / private key for encrypting communication. Passersby and tourists asked questions questions, shared a lot. Did Workshop : Name That Tech (where the picture is from)
The 15 gathered activists and hackers stood at a chalkboard in the street of the ancient district of Alfama in Lisbon as they did knoweldge shares around what the internet is, differences between circuit switching and packet switching. They were interested to understand protocol, IP, and public key / private key for encrypting communication. Passersby and tourists asked questions questions, shared a lot. Did Workshop : Name That Tech (where the picture is from)
Pierre, the organizer, really liked having a pre-set workshop (Name That Tech!) so he could spend more time on gathering people and the organizing. They’re excited to be a part of a larger community focused on these topics, and their next gathering will be based on doing as well as knowing, with a CryptoParty happening 15th of April: event link
Surveillance, how it pertains to us personally if you’re in a relationship.
These notes were co-taken in class, and I think they were awesome enough to merit posting to the class blog.
Speakers
– Sarah Cortes – a board member of Transition House, Tor researcher, and a PhD candidate working on anonymous networks.
– Andrew Lewman – a board member and executive director of the Tor Project, domestic violence advocate
Background Reading
Coercive control – 18 page summary
Tone and Terms
Domestic Violence. Violence is not the identifying factor of the problem. More of a myth and misconception that prevents people from understanding the underlying issue. Now it’s intimate partner abuse. Domestic is family – could be among many family members. Intimate partner abuse is just between intimate partners. Abuse means not just physical but also emotional, psychological, financial abuse, children. Many forms. Important to understand the terms we use.
Surveillance of government and partner abuse. Same concepts apply to both situations. One of the concepts in intimate partner abuse in the Western world is that intimate abuse is about a desire for control, due to an attitude of entitlement. Power and control. Similarly, a government’s surveillance is out of a desire for control and an a feeling of entitlement over citizens.
Entitlement
Entitlement in different societies, what are things you’re familiar with?
In intimate partner relationships.
If you think of them as their relative worth and needs and wants; if you think they have same relative worth and equal representation of needs and wants. In an abusive relationship, abusers feel their needs and wants and relative worth as significantly more prominent than their partner.
Abusers are people who have an attitude of entitlement over their partners. We see this same entitlement in class based systems, for example, the US class system.
We tend to magnify the opinions of wealthy people and denigrate the opinions of less wealthy.
In companies – there are different cultures. Entitlement is based on performance or different classes of people depending on a hierarchy.
In Japan, another example is seniority.
In England or the UK – they have a class-based system based on nobility and a peasant class.
Another concept that is important to understand is a lot of misconceptions.
That abuse is caused by alcoholism, drugs, that people who commit physical violence belong to a different category of abusers. That’s not actually true. One concept of abusers is that there is a continuum of abuse. There is a continuum of abuse – physical abuse on the far end and sexual abuse on the other with emotional, financial to academic, etc.
Continuum of Abuse
Abusers feel the need to exercise control over their abusers. They employ tactics, whatever works. Typically, they start out with a small tactic, and eventually destroy the self-esteem of the group who is being oppressed. Initially the person who is being abused doesn’t understand what is happening. In most situations, eventually, the victim will start to fight back. At that point, the abuser will step up to a new strategy, abusing children, financial abuse.
Eventually, a cycle ensues in which the victim steps up and fights back until the abuser is committing physical and sexual violence.
Often we see there is a pattern of abuse and other people, neighbors, bystanders will have noticed.

Let’s turn to governments and surveillance. The same value system will apply — certain groups are targeted nad denigrated.
Certain groups are denigrated and entitled groups feel entitled to surveillance. Surveillance starts out small but then takes smaller steps to include more groups.
Nushelle: If you have a system with a very vocal civil society – what happens?
We say we’re in a state of undemocratic democracy. (didn’t hear the rest…). If people fight back, step up, where there be higher levels of surveillance?
Manipulation and Excuse Making
Abusers in all forms make use of both of these
– 1945 (corporate interests, those who wanted to be reelected)
Civilians heard a different story: American fighting for democrac
Vietnam War, gulf of Tonkin Incident: http://en.wikipedia.org/wiki/Gulf_of_Tonkin_incident
Naval vessels came under attack from the North Vietnamese (FOIA reports later found that the second supposed attack, evidence was completely fabricated) to incite the public to support the war effort, escalating incidents but aren’t immediately clear. The idea is to divert people’s attention from what is really going on.
What is the cure/remedy
Due to attitudes and beliefs (women have less value, have certain characteristics), there is a belief then that that power and control has to be exercised over them, that other people have to continually to keep them under control.
The antidote is to change attitudes. courts started to
When governments perform surveillance – no one considers that it’s due to drug abuse or mental illness. It’s about belief in the inequality of those citizens.
Question and Answer
Question for those who have worked in domestic abuse in the past, is this type of training the same type of information you were given before? Or in sex ed class?
Q: What happens when people step up to new levels?
In governments we find a continual escalation. Eventually this sometimes leads to abused communities fighting back. But the abuser can never accept that the victim is actually being victimized. The response is seen as an encroachment on their own entitlement. The response is seen as an attack. So whether it’s governments, or abusive partners, it will continue sadly to escalate if it’s not checked.
How does this apply to this class?
In the same way we see things such as physical abuse more noticeable as emotional and psychological abuse, we see an act of physical violence as a tangible line which we can respond. In the same way, with surveillance it has been a slow escalation but now there are new revelations about the extent of surveillance.
U.S. has different capabilities. US has been swallowing not only metadata but all phone comms; with potential to do so in 6-7 countries. MYSTIC, revealed today in the Washington Post, from Edward Snowden’s leaked documents: http://www.washingtonpost.com/world/national-security/nsa-surveillance-program-reaches-into-the-past-to-retrieve-replay-phone-calls/2014/03/18/226d2646-ade9-11e3-a49e-76adc9210f19_story.html
Do we all believe that the US is collecting metadata on all communications in one country?
People think it’s possible but not sure it’s happening. Afghanistan, Pakistan are listed as possibilities.
But this news is met with ho-hum because people don’t see how it applies to them.
On slowly boiling frogs: http://en.wikipedia.org/wiki/Boiling_frog
Passing around book: Why Do They Kill
Where Does This Start?
Victims have no characteristics in common.
Targets of government system are pretty overt from race to class
Blaming the victim applies both to domestic abuse, and state surveillance: people assume ’they must have done something wrong.’
Children of abusers – you learn power and control from watching the dynamics of your parents, foster care, schooling, whatever, where there is a vast power dynamic between you and the people in your life. Origin of the attitude of entitlement.
Research has found this: children feel pity and sorrow for the victim, but side with the abuser because that’s who has the power and can take on the attitudes of that.
Father to son characteristics. If the father is an abuser – the son is more likely to be an abuser. If the whole society doesn’t respect women, you don’t need this direct tie.
What if both parties want power? Same sex relationships have the same incidence of abuse – so it’s not just men who have a desire for control.
Cambridge is interesting because it’s where the oldest houses are. And the oldest intervention program.
It was called the Batterer Intervention Program.
Why should we stop cyber stalking and immediate manifestation if you don’t attack the fundamental underlying reasons for it. Research that helps victims understand why their stalkers know where they are at all times rather than seeing them as an all powerful person.
Men will often select women because of their apparent inability to respond. So tech savvy male abusers are likely to capitalize on our society’s inclination towards women not being tech savvy. The abused often see their abusers as all-powerful. So teaching them about tech teaches them that they’re not all-powerful.
This is the same premise as why DiscoTechs are powerful and useful.
This post was written by Mariel of SocialTIC. Thanks, Mariel, for all the awesome work and the follow-up!
The 2012 elections brought political change in Mexico, and it hasn’t been positive in terms of State surveillance. At a time when threats to journalists and human rights defenders continue to increase, several reforms have been pushed in the federal and local congresses to make surveillance of private communications fair game. Behind legalese and political discussions that are anything but transparent, most citizens don’t realize what’s happening.
This is why action is necessary in Mexico: we need to raise awareness on the state of surveillance. And the Surveillance DiscoTech was a step in the right direction.
The DiscoTech in Mexico City began with a workshop on digital security focused on the basic ways individuals can protect their information (or at least make surveillance a much more difficult pursuit). All the participants had the chance to test email and chat clients that enable encryption, and learn the basics about digital security.
After the tech basics were covered, it was time to talk about the changing legal landscape, and about the surveillance projects that rarely make the local media. Luis Fernando García, human rights lawyer that works on freedom of expression and digital rights, talked about the current legislation. Despite the fact that private communications are, in theory, protected by law, government agencies have intervened more and more repeatedly since 2009. Last year, 700 interventions were carried out; this year, we are at 12000 already.
Congresses are passing a lot of reforms that force telecom companies to retain data indefinitely, that grant government offices access to anyone’s communications without a judiciary order, and that justify surveillance by claiming it’s all done in the best interest of those at risk (like human trafficking victims). These modified laws seem to have no checks and balances. The surveillance possibilities that are being granted by law are highly invasive, secret, and will certainly make a lot of money for a few companies.
Jesús Robles Maloof, human rights defender and lawyer, talked about the surveillance projects that rarely make the news: for example, FinFisher, a malware found in Mexican computers and that is believed to have been bought by an agency in the Mexican government. He also posed questions that, after a day of tech training, left all of us with food for thought: should we keep trying to race against the government by becoming better at using technology, or, in fact, is it a race we will lose? Should we focus instead on the main problem, which is to eradicate State surveillance?
Click CC for translation captions
Sasha Costanza-Chock also joined this discussion to talk about his research and the reasons why this DiscoTech was organized and then celebrated in different locations.
The Mexico City DiscoTech saw hands-on learning and discussion among people who are targeted by surveillance. One of the closing remarks came from a human rights defender who decided to share her conclusions on the DiscoTech: having learned about different aspects of surveillance, she would walk away aware of the need to be more mindful of how she uses technologies, no matter what they are or what she’s doing with them.
In our opinion, mission accomplished.
—
SocialTIC is a non-profit organization that works to promote the use of ICTs for social change in Mexico and Latin America. We work on information-based activism, digital security and data analysis with NGOs, human rights defenders, journalists, local groups and engaged citizens. You can follow us on Twitter.
Has it already been two weeks? Holy wow.
I’ll be aggregating the summaries from the Countersurveillance DiscoTechs across the world over the next week. This first one is easy enough, because I was there! This post shamelessly yoinked from my own blog, with mild adaptations.
With the Codesign Studio I TA with the Media Lab, a series of Discovery Technology (DiscoTech) Workshops were put on. The ones in Bangalore, Ramallah, Mexico City, Boston, and San Francisco were all inspiring. You can see more about the projects, art, and progress over on our hackpad. Some examples were stories from Venezuelan activists, face painting to deter facial recognition (so hard!), long-time surveillance on poor communities in America, and spoofing DNA.
And seriously. Take a few minutes to go through the partner pages for this. Need a bit of morning outrage? Think everything’s going pretty ok in the world? Nope!
The second usability hackathon with OpenITP went incredibly well, and repped as the San Francisco DiscoTech as well as its own thing.
The number of projects worked on is impressive, to say the least. You can read more about the objectives of the sprint and what was accomplished via the associated links.
The Guardian Project creates easy-to-use open source apps, mobile OS security enhancements, and customized mobile devices for people around the world to help them communicate more freely, and protect themselves from intrusion and monitoring.
Commotion is an open-source communication toolkit that uses mobile phones, computers, and other wireless devices such as routers to make it possible for communities to set up decentralized mesh networks and share local services. Deployed already in a handful of U.S. cities and internationally, it is a key tool for internet freedom, providing alternatives where surveillance and censorship compromise traditional infrastructure.
Martus is a secure and open-source human rights documentation system used by human rights initiatives to document and preserve evidence and testimonies of human rights violations.
StoryMaker is an open source app for making and publishing multimedia stories with any Android phone or device, as safely and securely as possible. It provides an interactive storytelling training guide, walkthroughs, and templates for users to follow as they plan their story and capture media. The app then helps assemble the content into a finished format that can be shared directly with social media or anywhere– no computer editing station required, even for video!
Lantern is a network of people working together to defeat internet censorship around the world. Install and share Lantern, our new peer-to-peer censorship circumvention software, to give or get access to people in places where access is censored
Serval is a telecommunications system comprised of at least two mobile phones that are able to work outside of regular mobile phone tower range due thanks to the Serval App and Serval Mesh.
ChatSecure is a free and open source encrypted chat client for iPhone and Android that supports OTR encryption over XMPP. ChatSecure was originally available for only iOS devices, but is now also available on Android via The Guardian Project’s similar app, formerly named Gibberbot.
Whisper Systems produces simple and easy-to-use tools for secure mobile communication and secure mobile storage. Their products include RedPhone and TextSecure, which allow encrypted VoIP phone and text (SMS) communication between users
People’s Intelligence is an award winning idea that makes use of USSD, SMS and voice to establish a conversation with victims and witnesses of mass atrocities. The envisaged tool helps victims and witnesses to better document and verify their stories and provides them as well as relevant organisations with actionable information, thereby facilitating early warning and targeted assistance. It supports analysis and allows networking between affected communities, relevant organisations and experts through the use of ubiquitous technologies.
Mailvelope allows individuals to encrypt and decrypt email in their favorite webmail provider following the OpenPGP standard. This includes, among others, Gmail, Yahoo, Outlook.com, and GMX. It integrates directly into the webmail user interface; its elements are non-intrusive and easy to use in a user’s regular workflow.
It was really nice to completely surrounded by the people I usually see when we all jam into the one or two sessions at any tech or policy event which involve both. But that overlap was the whole conference, so we were able to dive in much deeper, see more nuance, and see next steps. I learned about funder motives, and the initiatives which backed tech in atrocity prevention/detection/accountability, and about many many tools used to amplify the voices of marginalized people. I drew a lot, and I hugged even more.
Full set on bl00viz.
I typed notes for two interactive sessions for sake of formatting. One was a review of the the UI/UX hackathon the weekend before, the other was stories from the field and suggestions for how to be better trainers. Those can be found over on the Civic blog.
Thursday I trekked out to Oakland to participate in Engine Room‘s Responsible Data Forum, as hosted by the inspirational Aspiration Tech. Again, I was spoiled by being surrounded by an impressively diverse set of people interested in the same fulcrum of concern and change. We skeletoned out plans for checklists before collecting data, and workflows that include project death, and illustrated how data moves through a company. We talked hosting and coercion resistant design and informed consent. We also talked about context-based privacy in disasters. I’m looking forward to seeing what comes of the day.
link to the hackpad version of this post
When you are designing a project for social justice, where do you start?
In this workshop, we practice value-based design, a method that helps us to design for large scale social impact and to relate this directly to how we plan and implement projects. We envision the impacts we’d like to contribute to in the world and the values we bring with us into our work as the first steps in this design process. As individuals, this method helps us to express our connection to our projects on a personal level and to prevent burnout as we are able to identify work that resonates with our values and to set aside work that doesn’t. As a team, this method helps us to identify shared values and to make design decisions based on our shared vision instead of personal preferences.
At the last Codesign Studio, Bex and Willow took the class through an hour-long workshop to identify our individual values and to design our projects and approach around shared values.
This workshop is inspired by Monica Sharma’s work in transformational leadership for large scale system shift. In this article, she describes the framework of the methods she shares for this kind of work. Connecting with our personal values and designing based on values is a key component. [Sharma, Monica. “Contemporary Leaders of Courage and Compassion: Competencies and Inner Capacities.” Kosmos Summer 2012.]
Individual Values
Purpose
Uncovering our core values gives us better understanding of our own purpose and desire in the world. Doing this exercise with teammates is a great way to connect to each other’s inspiration.
Process
(3 min) Select one person in the room to work these questions with:
Share something you’ve worked on that you had some role in designing.
Ask the following questions:
(12 min) Now, break into pairs. If there are project teams in the room, ask people to work with someone in the same team and ask each other the questions above.
(at 6 min) Remind people to switch
Reportback
Have each person say their value when you reconvene. If you can, write these somewhere that will be visible for your team as you continue to work together.
Value-Based Design
Purpose
Designing a project with the larger purpose in mind helps to think big and understand that your actions connect to your visions of social justice. It also helps your team to recognize shared values, a great starting place for connecting when you have to make difficult design decisions.
Overview (5 minutes)
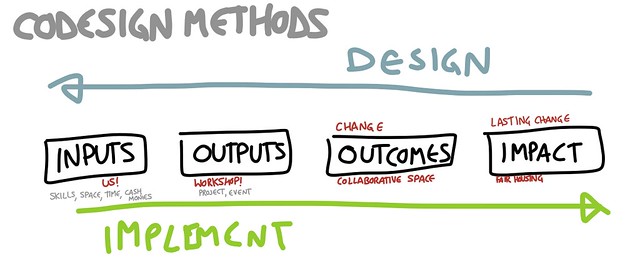
In this method, we design with our teams first by developing shared understanding of the impacts we want to see as a result of the work we do together. These will be large-scale and will likely relate to values we identified in the Individual Values exercise. In this exercise, Impacts, longterm sustained state change.
Because we can’t implement impacts directly, we continue to design our work into pieces of work that we can implement. We divide these pieces into three categories: Inputs, Outputs, and Outcomes.
Process
Share the above graphic.
Go through an example, here is an example of how we might have used this methodology in developing Codesign:
Ask what desired impacts of Codesign are:
Ask what some inputs, outputs and outcomes are of Codesign:
We tend to fill these three categories with information in a nonlinear way — recognizing an Output may surface desired Outcomes and Inputs. Broadly, we design right to left and implement left to right.
Project Design (25 min)
Now practice the value-based design methodology with project with your team. If you are at an early stage in your work together and you haven’t yet identified or selected a project you will work on, you can begin by taking the various partner’s organizational values into consideration. Broadly, what are the impacts that your team’s members envision?
Before completing the exercise, have each group fill in at least 2 points under each section.
Wrap It Up
Reportback (15 min)
Ask people to share their process. Try using the Green/Yellow/Red method and ask each group to share one Green – a thing that was easy or clear; Yellow – one thing that was challenging or that they learned something from; and Red – something that was difficult or a block.
If the teams went to different parts of the room, have everyone tour around. Document the work of each group.
Place It! founder James Rojas worked with the studio on codesign around cities and municipalities. He explained that one of the biggest challenges with urban planning is people and planners speaking different languages. How can planners understand people on their own terms? How do you communicate ideas in public meetings? What are alternative spaces for sharing ideas and working with people? Starting those conversations nonverbally allows participants to move beyond language barriers, perceptions of expertise, and their own cognitive blocks.
Postcolonial computing: a lens on design and development. In Proceedings of the 28th international conference on Human factors in computing systems
“Codesign in a historical context”
“A software design manifesto”
“Human Centered Design Considered Harmful”
As we enter into the codesign projects and processes, we need to think about it means to develop a project or technology with another group of people?
Much of the conversation revolved around the immediate production of results, which might not involve the community nor have lasting impact, versus long-term and nebulous projects. There are a lot of pressures that push people into short-term unsustainable solutions including time and energy, capital, the fact that solutions to the most complicated problems are often much more messy, personal interest, and individual trajectory. It’s easy to build a portfolio off of such items. This is in juxtaposition to “I worked with this community for three years and we tried to organized and go against this big company…” It’s not easy and really challenging. A balance is projects telling their story around the process of determining and delivering deliverables with things like video and blog posts.
And finally, we formed teams around the 4 community projects for the Codesign Studio. Each group took time to sync schedules and start planning their approach. The four projects are: Zumix, Urbano, City Life/Vida Urbana, and Brazilian Immigrant Center + REV. Each team is responsible for visiting their location at least 3 times over the course and will report their progress on this blog. We’re super excited to see what they come up with!