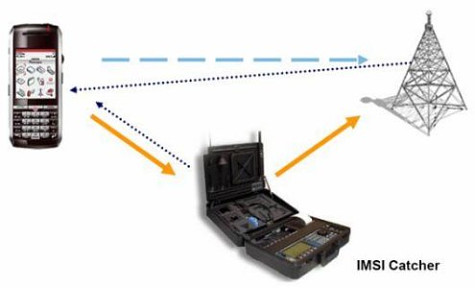
At this discotech, we showed visitors http://fuerza.is: an interactive checklist to help a victim determine whether their various devices are infected and being used in their stalking. Then we discussed scenarios and potential solutions for stalking via digital communication tools. A visitor came up with the idea of collecting app fingerprints. Even if it is less likely to be delivered at the term end, it exemplify how existing product helps framing the problem.
Another workshop held in the DiscoTech was explaining encryption. Activities included showing how to fake an email on behalf of somebody else (via shell script), using GPGTools to sign emails, and using GPGTools and AESCrypt to encrypt files. The workshop also included trying to use RetroShare (a P2P communication tool encrypted under PGP), but it didn’t work out.
We also had some conversations with some of the guests on actions they would take if they noticed they were being digitally surveilled. What steps would they take. We also went through some of the source of data around abuse and which of those cases may have a digital surveillance component. Among conversations we had regarding possible tools, is a digital application fingerprinting software that could detect changes in applications or changes in the behavior of some of the applications and how that could be used to inform users of threats possible. The other application we brainstormed about was on an activity log, resident on the phone that tracks a users actions and phone operations. A technique akin to self surveillance which would then help one in curating and identifying suspicious behavior.
In the team meeting this week, we drafted three personas of users, in which we will pick one to work on. They are:
- Advocates
- their ages range from teenager through elders
- their technical skills vary.
- They work at shelter organizations, generally focusing on all aspects of abuse and victim safety. Their focus is not on technology.
- When they are working, they are assigned to clients when they seek for help. During the help, they try to gain information from the client including feeling and mental status. Establishing the victim’s trust may take a long time.
- They need to assess the dangerousness of the victim’s situation quickly, in order to determine the best course of action for the victim.
- Victims
- They are possibly stalked by someone they know.
- The stalker generally is an intimate partner, co-worker, or a fellow student. They use technology in stalking as a way to exert control.
- A victim could be male or female – though females are more likely to seek help.
- The victim generally has little technology understanding. The stalker surveilling them only has to be more technology aware than the victim.
- They need to figure out what’s happening – build a picture of what’s happening.
- They are not sure about when it started and how often it is happening. Information on anything they feel threatening can be helpful to alleviate their suffering.
- By-standers
- They are any third party to the stalker and victim.
- Friends or family members of the victim could be the most helpful.
- The victim generally only hints at the surveillance to friends or family as a quiet plea for help.
- Once aware of the problem, a bystander is in the best position to get involved and do something to support the victim.
- One thing they can do is tell the victim’s situation to somebody in authority – See something, say something.