Magento 1.x Security Patch Notice
For Magento Open Source 1.5 to 1.9, Magento is providing software security patches through June 2020 to ensure those sites remain secure and compliant. Visit our information page for more details about our software maintenance policy and other considerations for your business.
Content Permissions
As a security measure, Magento includes a whitelist of content that can be referenced by custom modules and extensions. Some implementations such as blog extensions, reference content that can be accessed only if the directive is in the whitelist. For example, a module or extension might include the following markup tags on CMS pages or in email templates. For an example, see: Listing Categories On Home Page.
-
Commonly Used Directives {{config path=”web/unsecure/base_url”}}{{block type=rss/order_new}}
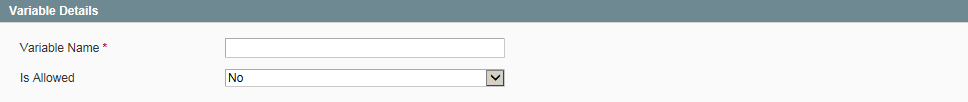
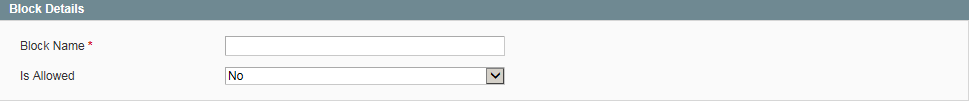
You can add the most commonly used variable and block references to the whitelist from the Admin. If not included in the list of allowed directives, it must be added to the database installation script on the server. Some configuration variables or blocks can be added to the whitelist only by running a data update script that lists each additional directive.
-
Variable and Block Names in Script permission_variablepermission_block
-
Allowed Directives Content References
Variables
web/unsecure/base_urlweb/secure/base_urltrans_email/ident_support/nametrans_email/ident_support/emailtrans_email/ident_general/nametrans_email/ident_sales/nametrans_email/ident_sales/emailtrans_email/ident_custom1/nametrans_email/ident_custom1/emailtrans_email/ident_custom2/nametrans_email/ident_custom2/emailgeneral/store_information/namegeneral/store_information/phonegeneral/store_information/addressBlocks
core/templatecatalog/product_new